It was 09/24/2019 I was newbie at bug bounty hunting, though I’m still newbie there! Whatever, let’s enter the story.
Today I gonna share about the SSRF vulnerability. Let’s know what is SSRF. Server-side request forgery (also known as SSRF) is a web security vulnerability that allows an attacker to induce the server-side application to make HTTP requests to an arbitrary domain of the attacker’s choosing.
Okay, When I just started my hacking life, I liked to test random websites to improve my skill because I was not enough for test on a platformed website. I took a Bangladeshi well known E-Commence website for my testing. I just started an got a request like this.

The request is calling another cross domains data with thw ‘src’ parameter! Hmm..!!! I just changed the URL and didn’t understand whats happened! Then I made an php file on my previously randomshelled domain with a JavaScript contents “<script>alert(document.domain)</script>”. Replaced the URL with the JavaScript URL and the request was like this.

I became very strange! It was working! The response was like this!

The request was loading file from third party domains!
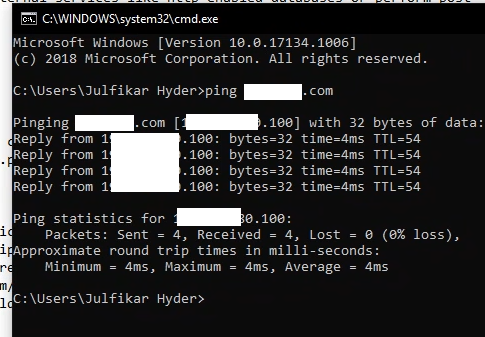
Then I started to think what can I do more, what can I do more! Because I had no IP logger that I can check the SSRF clearly! I fired up MY little buddy Command Prompt and took the IP of my target domain with the command ‘ping targetsite.com’.

I again changed the request like this,

I changed the URL with Iplocation got the domain’s IP at the response!

SSRF confirmed again!
The site had no bug bounty program, but I reported them politely and they awarded me with 10000৳ which was unexpected even they didn’t have any bounty program! 😀 !
Additional resource: https://www.wizcase.com/tools/whats-my-ip/
Everyone loves what you guys are usually up too.
This type of clever work and coverage! Keep up the fantastic
works guys I’ve you guys to my blogroll.
Fixed. And thanks for you feedback.