Hey hackers! I hope you’re all doing well! Here I am back with another write-up of an easy XSS I found on the University of Cambridge’s website! The bypass or payload was too easy, but finding a valid web security vulnerability in Cambridge makes me feel proud, and that’s why I’m writing this. Although I was acknowledged by Cambridge University for finding a P1 (critical) vulnerability before achievements. The vulnerability was that I could retrieve all the raw requests that were passing to the server!
Whatever the date was, it was March 12th. Mohammad Golam Rabbi, one of my juniors at BugBounty, had tagged me on Facebook. He was asking for a solution to an XSS he was trying on Cambridge’s website. I checked his payload, which seemed correct, but the pop-up wasn’t firing!
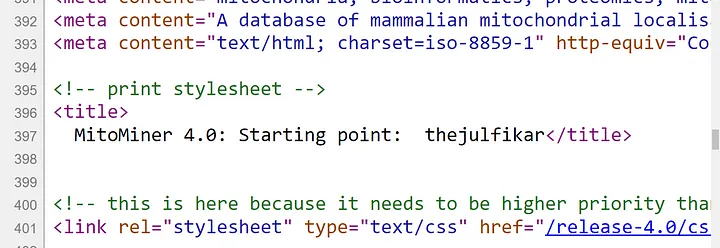
I crawled his shared URL and got an endpoint like this: “https://localhost/release-4.0/aspect.do?name=“. I tried with the string “thejulfikar” and got a response like this:

This response made me smile!
The string ‘thejulfikar’ was reflecting in the <title> tag, and whatever we enter at the ‘name=’ parameter will reflect in the <title> tag! So, what do we need to do? To trigger an XSS here, we just have to close the tag. We can achieve this by inserting ‘</title>’ before the string. I checked the response again, which was like this:

As you can see here, the tag got triggered successfully! Now we can insert our payload here, and we don’t have to worry about the next part or the next ‘</title>’ tag because we’re closing our payload here!
Then I simply entered the payload ‘<script>alert(“XSS by thejulfikar”)</script>’ into the ‘name’ parameter.

I rendered the request to my client, and XSS got triggered!


Howdy just wanted to give you a quick heads up. The text
in your post seem to be running off the screen in Firefox.
I’m not sure if this is a formatting issue or something
to do with web browser compatibility but I thought
I’d post to let you know. The design and style look
great though! Hope you get the problem resolved soon. Thanks
Fixed. And thanks for you feedback.